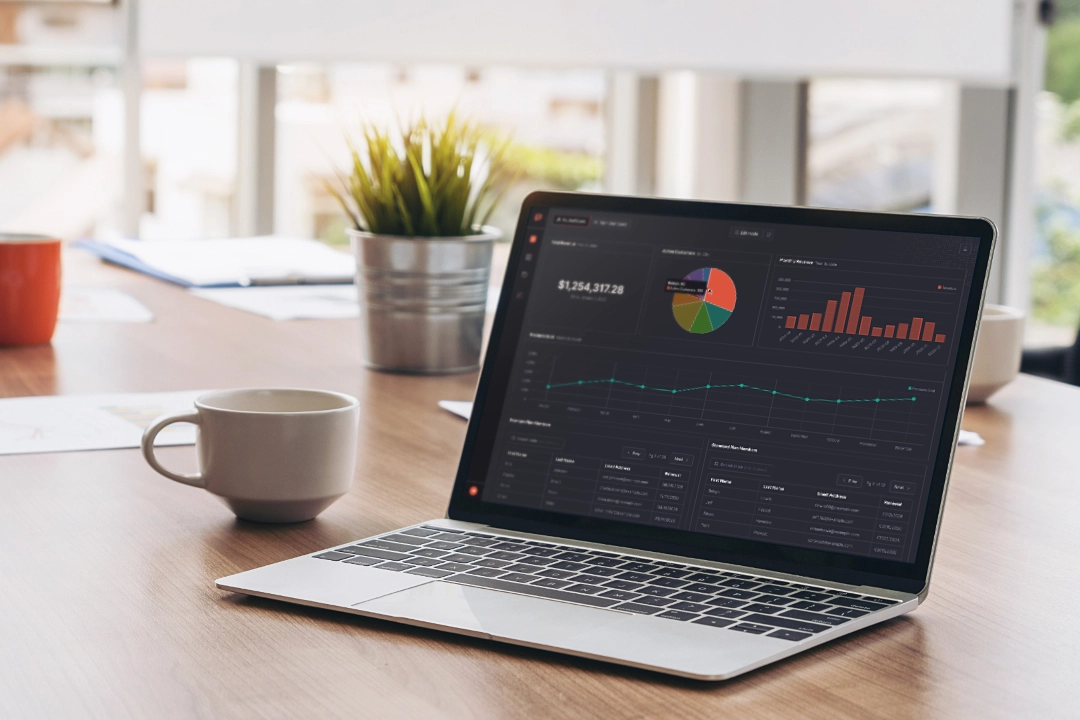
When teams evaluate an analytics tool, they are not searching for features.
They are evaluating risk.
They want to understand what happens when the system connects to their data.
They want to know what it can do, what it cannot do, and what happens when something feels unexpected.
Most of all, they want to know whether they will still recognize their data environment after the tool has been in place for a while.
Teela was designed with those expectations in mind.
Security and transparency are not framed as safeguards layered on top of analytics.
They are the design constraints that shape how Teela works at every level.
The goal is simple: answers should arrive quickly, and trust should remain intact long after they do.
A Clear Boundary Around Your Data
Teela is read-only by design.
It does not write to your database. It cannot modify production data.
Queries that attempt to insert, update, delete, or alter records are blocked at the system level and logged automatically.
By removing the ability to write data entirely, Teela eliminates a class of risk that often forces teams to slow down or second-guess their own questions.
Exploration becomes safe by default. Curiosity does not require caution.
Teams can ask more questions because the system has clear limits.
Keeping Data Where It Belongs
Teela operates inside your environment.
Your data is not exported for processing.
It is not sent to third-party services. It is not used to train models or stored elsewhere for analysis.
There are no background syncs or hidden pipelines moving information outside your control.
The system works with your data where it already lives.
This approach favors containment over convenience. It reduces surface area. It simplifies oversight.
And it allows teams to adopt advanced analytics without introducing uncertainty about where their information goes or who might have access to it.

Security as a Baseline, Not a Feature
All data in transit is protected with military-grade encryption.
Credentials and connection details are always masked and never exposed in plain text.
Not during setup. Not in logs. Not in shared views.
This level of protection is treated as foundational, not optional.
It exists so teams can focus on decisions instead of defenses.
Access That Reflects Real Teams
Teela uses granular, explicit permissioning.
Administrators define access by user, folder, DataClip, or dashboard. Sensitive financial or operational data can be limited to specific roles without restricting visibility elsewhere.
Permissions do not drift over time. Changes are intentional, and every change is recorded.
The result is a system that mirrors how organizations actually operate, where responsibility and visibility are not evenly distributed but clearly defined.
Answers That Can Be Inspected
Most analytics tools stop at the answer.
Teela does not.
When a user asks a question, Teela makes its reasoning visible.
The system records how it interpreted the request, which paths it evaluated, and how it arrived at the final query. That activity is captured in an Activity Log that shows each step in the process.
This allows users to see how the system worked through the question. Not as an abstract explanation, but as a clear sequence of decisions.
Once an answer is returned, Teela goes further.
Every result includes access to a SQL Log that shows exactly which tables were queried, how they were joined, and what filters were applied to produce the answer.
Users can inspect the query, validate the logic, and understand how the data was assembled.
Nothing is hidden behind a black box. Answers are not just delivered. They are explained.
This visibility is available to the people using the system, not reserved for administrators. When numbers change, teams can see why. When results raise questions, the path to verification is clear.
Nothing is hidden behind a black box. Answers are not just delivered. They are explained.
Language as a Tool for Accuracy
Data errors often begin with misalignment between business language and technical structure.
Teela reduces that gap during onboarding by learning how your organization describes its work. Clients, customers, revenue, projects, locations. The terms your teams already use become the terms the system understands.
That language carries through every interaction, including how queries are interpreted and logged.
By grounding questions in familiar vocabulary, Teela reduces misinterpretation before it happens. The system asks better questions because it understands the business context behind them.
The result is fewer assumptions, fewer silent errors, and greater confidence in the answers that drive decisions.
Nothing Happens Quietly
Teela is explicit by design.
Connections are initiated manually. Authentication is deliberate and recurring. Attempts to perform restricted actions are blocked and explained.
Every meaningful action is captured in logs that can be reviewed later. Queries, permissions, activity. If something happens, there is a record of it.
There are no hidden integrations. No silent background behavior. No unexplained data movement.
Everything the system does is visible, traceable, and intentional.
Built for Trust That Lasts
Teela is not designed to create confidence in a single moment.
It is designed to maintain trust over time.
As teams grow. As questions evolve. As new people rely on existing data.
Security and transparency are what allow analytics to remain useful as organizations change.
They make answers repeatable, explainable, and defensible.
Teela’s role is straightforward.
Protect the systems behind the data. Make reasoning visible to the people who depend on it.
And deliver answers without compromising control.
That commitment is not expressed through promises.
It is expressed through how the product works.
Get to know your data.
Safely.